These capabilities include day one provisioning, day two management, and beyond. If your organisation manages cloud infrastructure but isn't using Terraform, it's definitely time you checked it out. The only way to manage cloud infrastructure at scale is via automated provisioning and managing, building your workflows and security in from the beginning. While alternate cloud-specific products exist, provisioning and managing infrastructure in a multi-cloud environment brings its own set of challenges, and this is where Terraform is uniquely placed to give your organisation a single multi-cloud automation solution.
Not only does this include scripting your environment in the first place, but detecting drift - once the infrastructure is provisioned it can be challenging to ensure the actual state of resources always reflects the recorded, desired state and health. What worked at the time of provisioning - including configuration and IAM - may not continue working properly post-deployment.
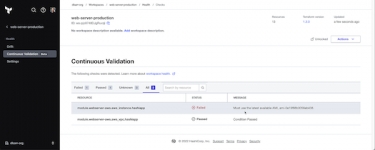
HashiCorp has announced drift detection to continually check infrastructure state to detect changes and provide alerts. Announced today, continuous validation also expands checks on your infrastructure beyond configuration drift - it provides long-term visibility and checks of your infrastructure's health and lets users add assertions to ensure these pre- or post-conditions are continually passing validation. Terraform will notify users when an assertion fails, minimising risk, downtime, and costs.
|
|
Additional announcements include no-code provisioning. The 2022 HashiCorp State of Cloud Strategy Survey found skills shortages were ranked as the top multi-cloud barrier for technology practitioners and decision-makers. Traditionally, provisioning something immediately useful with Terraform requires knowledge of infrastructure or networking as well as familiarity with HashiCorp Configuration Language (HCL), which can create a barrier to adoption.
The introduction of the private registry for Terraform Cloud and Terraform Enterprise made it easy to publish validated and approved modules that can be reused throughout the organization. But this degree of self-service only goes so far, as developers still have to select a module based on its contents, add it to a version control repo, create a workspace in Terraform Cloud, and provision the module from that workspace.
Given all of this, HashiCorp wanted to offer greater self-service capabilities with a new no-code provisioning workflow. In addition, letting users avoid these various processes could reduce the number of people you need to train in Terraform.
Thus, announced today, Terraform now offers no-code provisioning - allowing administrators and module publishers to manage a catalogue of no-code-ready modules for users like application developers to deploy directly to workspaces. Developers can self-serve infrastructure from the Terraform private registry by selecting the no-code-ready module they need, entering the required variables, and deploying directly into a new workspace - all without writing HCL. Platform teams can now spend less time servicing repetitive internal requests and spend more time building on existing work to drive innovation and support the business.
End users can now find no-code modules from their organization’s private registry.
Additionally, HashiCorp announced managed open policy agent (OPA) for Terraform Cloud. As organisations grow in size and infrastructure complexity they face increased risks of security breaches and non-compliance with regulatory compliance. HashiCorp previously released Sentinel, a policy as code framework, and in August of this year, HashiCorp added Sentinel policies to the Terraform Registry so that experts can create and share reusable policies with the rest of their organisation.
Today's announcement introduces managed Open Policy Agent (OPA) for Terraform Cloud, which extends the policy as code features of Terraform Cloud to support OPA, based on the Rego policy language. Support for OPA in Terraform allows customers who have already standardised on OPA to bring those policies along with them into Terraform Cloud. OPA works alongside Sentinel to increase the number of supported ways for customers to adopt a policy as code framework for secure multi-cloud provisioning.
Now you can see if your OPA policies have passed or failed within Terraform Cloud.
Other announcements include
- availability of the Azure Provider Automation tool
- ServiceNow ServiceGraph connected
- Terraform Plugin framework (beta)
You can sign up to Terraform for free and also learn more via a Set up a No-Code Provisioning Workflow with Terraform Cloud webinar on Tuesday 1 Nov 2022.