Eclypsium, is the digital supply chain security company protecting critical hardware, firmware, and software, today announced the industry’s first solution that measures the risk of IT infrastructure, including laptops, desktops, servers, network equipment, IoT devices, and software. CIOs, CISOs, and supply chain leaders can use the Eclypsium Guide to Supply Chain Security to make more cost-effective and risk-based purchase decisions, as well as assess their exposure to new supply chain cybersecurity incidents.
“Digital supply chain security is a board-level concern for many organizations, and there is an urgent need to provide a central repository for organizations to assess IT product risk,” says Eclypsium CEO and Co-founder Yuriy Bulygin. “Eclypsium is able to provide this supply chain intelligence because we have the deepest and broadest library of third-party hardware, firmware, and software component risk data.”
According to Gartner, by 2025, 60% of supply chain risk management leaders plan to use cybersecurity risk as a significant determinant in conducting third-party transactions and business engagements. The new Eclypsium Guide meets the need for more quantifiable data during supply chain risk assessments.
“Supply chain threats exploit the intricate network of trust inherent in the technology ecosystem we rely on today. Within this ecosystem, every piece of equipment, application, and cloud service is a culmination of highly specialized, interdependent components sourced from various suppliers,” says Ramy Houssaini, a senior Digital Trust executive and chair of The Cyber Poverty Line Institute. “It is crucial for us to have a full stack view of the vulnerabilities inherent in this complex ecosystem and to take proactive measures by utilizing technology that can provide risk intelligence on IT infrastructure.”
Already in 2023, there have been a number of supply chain incidents that affect IT infrastructure:
Ransomware groups, including ALPHV, BlackCat, FIN8, and LockBit, targeted vulnerabilities in network infrastructure devices and virtualization infrastructure.
BlackLotus, Volt Typhoon, and BlackTech threat actors took aim at the firmware supply chain of PCs, servers, and network equipment by multiple manufacturers as an initial access vector and to establish persistence.
Ransomware gangs breached major infrastructure vendors, including TSMC, MSI, and Western Digital, exposing sensitive information about their products that could be used by attackers to develop supply chain attacks.
Security incidents with wide impact highlighted serious weaknesses in the enterprise infrastructure supply chain, such as: vulnerabilities in MOVEit by Progress Software; firmware backdoor capabilities in Gigabyte systems; vulnerabilities in remote management components used by most major server manufacturers; network infrastructure vulnerabilities like Citrix Bleed; hardware vulnerabilities like Downfall, Zenbleed, and other vulnerabilities in CPU components; and disk drive components used in U.S. government agencies manufactured by a company with ties to the PRC’s PLA.
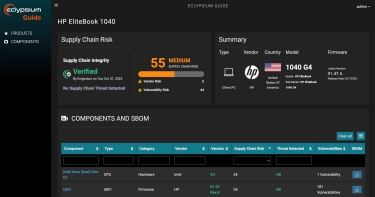
The Eclypsium Guide will equip IT, security, and procurement teams to track these types of supply chain risks and incidents and see if products that they use or are considering purchasing are affected. At launch, the Guide includes verified details about products and components of hardware and software vendors, including Dell, HP, Lenovo, HPE, Cisco, Intel, AMD, NVIDIA, and others. It will be available as a standalone SaaS offering that is complementary to and integrated with the Eclypsium Supply Chain Security Platform.
To schedule a demo of the new Eclypsium Guide or the Eclypsium supply chain security platform, visit www.eclypsium.com or email your Eclypsium representative at sales@eclypsium.com.