Displaying items by tag: Application
Dematic launches new vision picking solution to the Australian and New Zealand supply chain industries
Dematic, a leading global supplier of integrated supply chain and warehouse automation technologies, software, and services, is excited to announce the launch of its innovative Vision Picking Solution in Australia and New Zealand. This advanced solution is designed to optimise warehouse worker productivity and enhance supply chain processes by integrating vision-assisted picking with real-time logistics solutions.
Western Australia Police ‘improves response to family violence’ with Motorola Solutions’ technology
Western Australia Police Force (WA Police Force) is helping its front-line police officers provide better support for victims of family violence through a smart mobile application from Motorola Solutions., which streamlines reporting and collaboration with partner agencies.
First Impressions Matter: Almost 70% of Australian Workers Abandon Job Applications Due to Complicated Recruitment Processes
GUEST RESEARCH: New research from Humanforce reveals almost 70% of Australian workers abandon job applications due to confusing or difficult recruitment processes. This alarming trend, where potential employees are disengaging from companies during, and sometimes before, their recruitment journey, poses a significant issue for employers operating in today’s extremely tight job market.
Cisco Secure Application makes it easier than ever to secure your cloud native applications and sensitive data
With Cisco Secure Application on the Cisco Observability Platform, customers have more flexibility and choice when it comes to tackling their most difficult security challenges.
The risks of mistaken conclusions and rushed actions during an outage
GUEST OPINION: When an outage or disruption occurs, there’s immediate uncertainty as to what happened, where and why. Uncertainty is inevitable in the early stages of any outage while root cause analysis is underway.
How To Get MS Outlook Data Repaired From a Vvew Virus Attack
Several people lose their Microsoft Outlook data because of Vvew virus attacks. Many people are unaware of the solutions to this problem and ultimately lose important information. At the same time, this is all they need to recover their files.
It is essential to note that the Vvew virus is an Avant virus that attacks computers through emails and website pages. It has layered blocks of designs used to attack, encode, and erase MS Outlook PST files. Once it strikes any .PST file, it alters its code and changes its extension to .vvew. Once this happens, you cannot use your Outlook files or mail because your MS Outlook reads files with .PST and OST extensions.
While the Vvew virus might seem harmful to files and data, the Recovery Toolbox for Outlook has powerful algorithms to scan every file from the email box and repair it. There are two methods to solve the problem with this tool. They are:
- The online method: https://outlook.recoverytoolbox.com/online/
- The offline method: https://outlook.recoverytoolbox.com/repair-outlook/
The two methods are workable to solve the virus attack because the tool has an online and offline version. You can use these versions to recover encrypted .PST files (.PST across all versions– ANSI (Outlook 97-2003), Unicode (2007 and above)).
Read through to understand how to recover and restore your Microsoft Outlook files.
The Online Method: How to Recover Your PST File with Recovery Toolbox for Outlook
You can easily use this to regain your affected information online. This recovery process works effectively on all devices as smoothly and swiftly as possible to restore OST files and fix your encrypted .PST files.
Follow these steps to repair your files online:
- You must change the file extension from Vvew to PST for the service to select the recovery algorithm to use.
- Click “Select file” and select an Outlook data file with the extension “.PST” or “.OST.”
- Input your valid email address
- Click Continue
- Wait for the corrupted .pst/.ost file to be recovered
- Download the recovered Microsoft Outlook pst file
Once you have recovered the data from the affected MS Outlook file, it will be stored as a new MS Outlook 2016 file with the .PST extension. This way, it will be easy to regain any .PST MS Outlook private file through any browser and device.
The Offline Method: How to Recover Your Infected .PST with Recovery Toolbox for Outlook
Before you begin, you must look for your Outlook Data Files in Outlook before repairing infected .pst files. Follow these steps
- First, select File, Choose Account Settings, and Click Account Settings.
- Next, select the Data Files
- You will see all Outlook Data Files (.PST) and Offline Data Files (.OST) listed, along with the account name the files are associated with.
Once you have been able to locate all your Outlook files, take these steps to repair your attacked file.
Step 1. Identify the infected Outlook data file location
To recover an infected Outlook data file, first Exit Microsoft Outlook and check one of these locations:
- For Outlook 365: C:\Users\Username\AppData\Local\Microsoft\Outlook\
- For Outlook 2019: C:\Documents and Settings\user\Local Settings\Application Data\Microsoft\Outlook
- For Outlook 2016: C:\Documents and Settings\user\Local Settings\Application Data\Microsoft\Outlook
- For Outlook 2013: C:\Documents and Settings\user\Local Settings\Application Data\Microsoft\Outlook
- For Outlook 2010: C:\Documents and Settings\user\Local Settings\Application Data\Microsoft\Outlook
- For Outlook 2007: C:\Documents and Settings\user\Local Settings\Application Data\Microsoft\Outlook
- For Outlook 2003: C:\Users\username\Documents\Outlook Files\
- For Outlook XP: C:\Documents and Settings\Username\Local Settings\Application Data\Microsoft\Outlook
- For Outlook 2000: C:\Documents and Settings\Username\Local Settings\Application Data\Microsoft\Outlook
Step 2: Download, install the program and Run it.
Step 3: Choose the file encrypted by the virus and select Next.
Step 4: Select Recovery Mode and Click Next.
Step 5: Click on Yes to begin recovery.
Step 6: Inspect the data preview and click Next to save the recovered file to a new location.
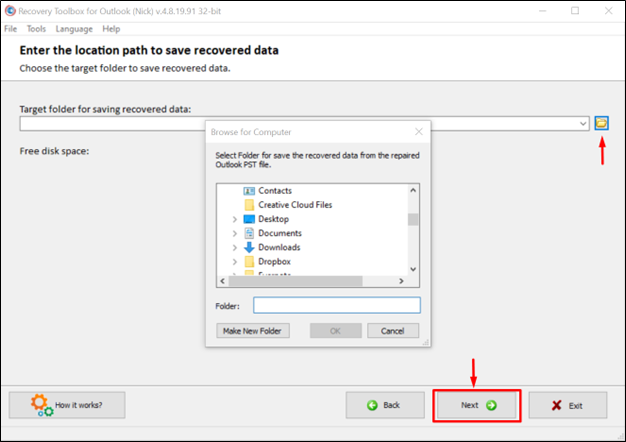
Step 7: Enter the location to save the .pst file and click Next.
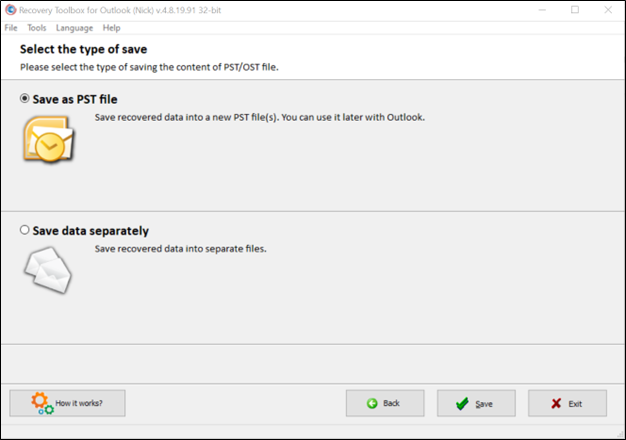
Step 8: Save the recovered data as the new .pst file.
Step 9: After checking the successful recovery results, click Finish to exit the Recovery Toolbox for Outlook tool.
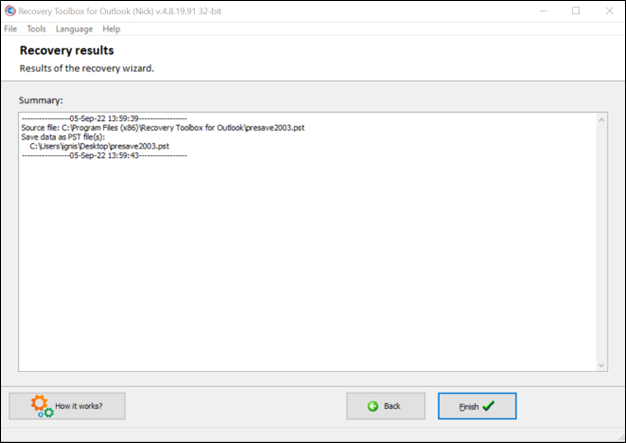
It is important to note that you should substitute the damaged file with a recovered one. You can also add the recovered .pst file to the list of data files in Outlook. This is how you do it for these versions of Outlook: 2021, 2019, 2016, and 2013:
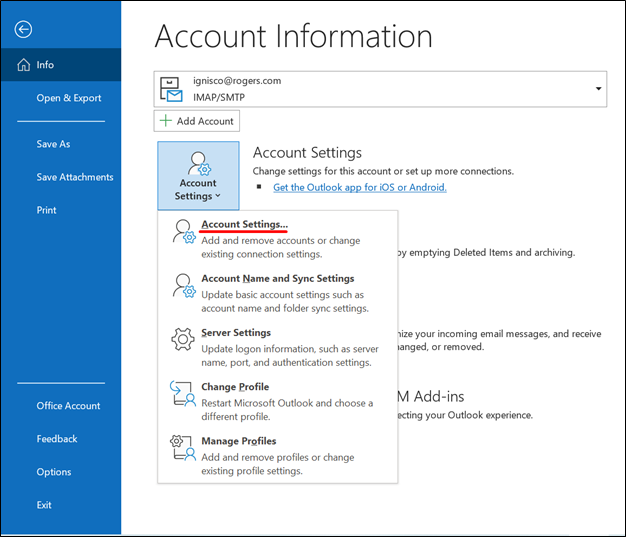
- Choose the menu item File | Info.
- Next, click the button Account Settings.
- Finally, choose Account Settings in the pop-up menu.
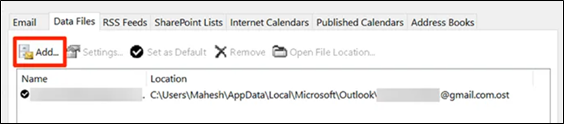
- Choose the Data Files tab and click Remove.
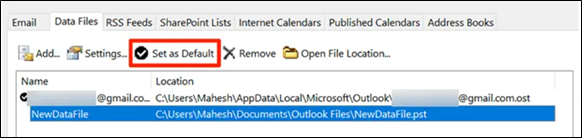
- Click Open File Location and select the recovered file. Click Set as Default.
Once you have reached this stage, you have successfully fixed the issue.
Conclusion
The Recovery Toolbox for Outlook uses high-grade algorithms and procedures in analyzing, fixing, and restoring files, irrespective of the problem or its cause– i.e., viruses, bugs, hardware damage, network problems, HDD damage, etc.
The tool has the following advantages:
- With the tool, you can fix Microsoft Outlook files with .PST extension across different versions (ANSI (Outlook 97-2003), Unicode (2007 and above)).
- The recovery tool allows you to repair and recover files protected by a password.
- With the tool, you can recover damaged (or attacked) OST files irrespective of their versions.
- The tool allows you to repair encrypted files with the .PST extension.
- You can quickly repair PST files of different sizes, up to 180 Gigabytes, and more.
The Recovery Toolbox for Outlook is very efficient for repairing and recovering every kind of file and data on Microsoft Outlook. You can use it to easily access damaged, password-protected, and encrypted files like contacts, tasks, documents, etc. The tool is easy to use and is effective both online and offline.
Radware expands DDoS protection for world-leading telecom
COMPANY NEWS Radware a leading provider of cyber security and application delivery solutions, has expanded its relationship with one of the top five largest telecommunications companies in the world ranked by revenue.
Dynatrace Achieves AWS Security Competency
COMPANY NEWS: Recognises the company’s unified observability and security platform as a trusted solution for helping organisations identify, resolve, and defend against threats to their AWS environments
Radware provides network and application security for busy airport
COMPANY NEWS: Radware (NASDAQ: RDWR), is a leading provider of cyber security and application delivery solutions, today announced that it was selected to provide network and application security to protect the data centres for one of North America’s top 20 busiest airports.
Radware to deliver advanced DDoS protection for data centre infrastructure of leading telecom
COMPANY NEWS: Radware (NASDAQ: RDWR), is a leading provider of cyber security and application delivery solutions, announced it signed an agreement with a leading European telecom and managed security service provider.
Is your Data Centre a ‘Carbonivore’?
GUEST OPINION: Sustainability has become a boardroom priority for modern organisations. Alongside the pressure of the ongoing climate crisis, there are good business reasons for this to be a focus.
Hitachi Vantara Unveils Hitachi Virtual Storage Platform One, Signifying a New Hybrid Cloud Approach to Data Storage
COMPANY NEWS: Single data platform will provide a simplified experience to consume and manage block, file, object, and mainframe data, with flexible consumption as an appliance or software-defined across public cloud and on-premises
Latest Dynatrace Platform Innovations Available to Customers on Microsoft Azure
COMPANY NEWS: Empower teams across organisations to collaborate, create, and share AI-driven analytics, apps, and automations for any business, development, security, or operations use case
The power of experiential content – how to maximise CX digitally and in-person to fast-track sales
GUEST ARTICLE : In today's competitive retail landscape, customer experience (CX) plays a pivotal role in driving sales and fostering brand loyalty. Experiential content has emerged as a powerful tool to create immersive and engaging customer interactions. So how can retail, ecommerce and online brands leverage CGI and 3D render technology to deliver market-leading customer experiences, both online and in physical stores?
Freshworks Unveils New Generative AI Enhancements Across Product Lines to Power Greater Business Efficiency
COMPANY NEWS: Freddy, Freshworks’ AI assistant, continues to advance to make generative AI more accessible to employees in support, sales, marketing and IT, making their everyday work easier
Absolute Software, Ivanti Neurons partner to ‘strengthen’ resiliency of Ivanti’s UEM solution
Self-healing endpoint and secure access solutions Absolute Software has announced a partnership with Ivanti to enable Absolute Resilience customers to strengthen the health and resiliency of Ivanti Neurons for Unified Endpoint Management through Absolute’s “unique” application persistence capabilities.
Checkmarx unveils context-aware Checkmarx Fusion with industry's first holistic view and cross-component prioritisation of application vulnerabilities
COMPANY NEWS: Developers and application security (AppSec) teams today have long needed a single, integrated view into the interaction, functions and vulnerabilities of the dozens of components in today’s typical application in order to perform comprehensive AppSec testing. In response to that need, Checkmarx, the global leader in developer-centric application security testing (AST) solutions, today announced the availability of Checkmarx Fusion, a context-aware correlation engine that enables full visibility into applications, component interactions, and bills of materials. It leverages a holistic view of application security scan results across all stages of the software lifecycle to correlate and prioritize vulnerabilities, thereby guiding remediation of the most critical issues first. Checkmarx Fusion is part of Checkmarx One, the industry’s most comprehensive application security testing (AST) platform.
Developing a custom app is good for your business - and here's why
GUEST OPINION: A good business is a business that is constantly growing - and that means keeping an eye on the future and continually innovating. With over 6.6 billion smartphones in the world one of the most popular marketing channels is a mobile app, and with 50% of companies owning their own app at least one of your competitors has already got on board.
Deloitte Australia launches new AI Institute
Professional services firm Deloitte Australia has launched its new AI Institute.
Five key drivers of unified fast file and fast object storage: the next step in the evolution of storage
GUEST OPINION by Sunil Chavan, Vice President, FlashBlade, Asia Pacific & Japan, Pure Storage: As applications that draw on file storage have grown more demanding, database applications have become more sophisticated, and the web, IoT, and demand for analytics have caused an explosion in the need for object storage.
WEBINARS & EVENTS
- APAC marketers' meetup: Turning customers into brand champions w/ FIFA Women’s World Cup’s head of marketing
- ManageEngine to host CyberCon Roadshow 2024 in Australia and New Zealand
- Jira Service Management Showcase - FREE EVENT TODAY
- Small Business Growth series: Marketing, mindsets, and lifecycles
- PRTG - learn how you can enhance PRTG using extensions while discovering best practices and tips for optimal PRTG usage
CYBERSECURITY
- Multi-million-dollar Deepfake Campaigns blocked by Gen
- Infoblox, Baidam launch fraudulent website takedown service
- Empowering the Next Generation: KnowBe4 Releases its Children’s Interactive Cybersecurity Activity Kit
- CyberArk Named Trusted Cloud Provider by Cloud Security Alliance
- ACMA alerts the public to be vigilant against romance scams
PEOPLE MOVES
- Armis appoints Christina Kemper to Vice President of International
- ECI Software Solutions appoints industry veteran Ray Wizbowski as chief marketing officer
- TBM Council Announces New Executive Director
- Pronto Software leadership changes to strengthen company operations
- Avalara Names Kevin Sellers Chief Marketing Officer
GUEST ARTICLES
- The impact of mental health on workplace productivity
- AI transforms the business of tender writing in Australia
- CyberArk Named a Leader in the 2024 Gartner Magic Quadrant for Privileged Access Management
- i-PRO establishes pioneering AI governance framework and ethics committee
- Datadog announces the general availability of Datadog Monitoring for Oracle Cloud infrastructure
- BeyondTrust Named a Leader in 2024 Gartner Magic Quadrant for Privileged Access Management
- Genetec Expands Security Centre SaaS With The Launch of Operations Center, The Industry’s First Work Management Solution For Physical Security Operations
- A third of businesses with excellent technology connectivity report being industry leaders in financial performance
- OutSystems and KPMG announce new survey exploring AI and the future of software development
- Fifty-five percent of OT environments contain four or more remote access tools, greatly expanding attack surface and operational complexity
Guest Opinion
- The impact of mental health on workplace productivity
- Why mid-size enterprises must prioritise loyalty to drive long-term success
- The ultimate guide to HWID spoofing: How to avoid bans and stay undetected
- Decoding return on investment of artificial intelligence and automation to unlock true value for every business
- Tenable patch Tuesday comment
-
How a quality defense attorney can help with a public intoxication charge
GUEST OPINION: Facing a public intoxication charge can be a…
-
The importance of writing and distributing press releases for your business
GUEST OPINION: Press releases have been a cornerstone of public…
- New Australian AI framework for government helps close the trust gap
- Why Insider Threats Are A Growing Challenge For Organisations
- How investing in Conversational AI could enable your HR department to stay on top of its remit in FY2025
ITWIRETV & INTERVIEWS
- iTWire Learns How Zoho’s ManageEngine Views Ai-Powered Cyberthreats
- iTWire Learns About Norwegian Video Conferencing Company, Neat
- iTWire talks to Hitachi Vantara's ANZ MD
- iTWire learns about HID’s latest frictionless identification & access tech
- iTWire interviews Milestone & learns the latest about its Video Management Software (VMS)
RESEARCH & CASE STUDIES
Channel News
Comments
-
Re: iTWire - Assange freed after US plea deal, expected back home
Everyone got a bit of what they wanted. No one got everything, that sounds like the basis for a good[…]
-
Re: iTWire - ZeroGPT.com: The Ultimate Suite for AI Text Detection and Beyond
Is this article ironic?
-
Re: iTWire - Five Australians held in operation to take down cyber-crime ring
The safest way not to get snared is to avoid anything financial on your devices plus do not participate in[…]
-
Re: iTWire - "Not us" - Snowflake wrongly implicated in Ticketmaster leak
Who do we trust here? A professional cloud provider with many customers or a monopolistic ticketing agency that can never[…]
-
Re: iTWire - There are some idiot ‘hackers’ out there!
I knew this scam was full of shit because it didn't present any actual evidence of the supposed hacker having[…]








































